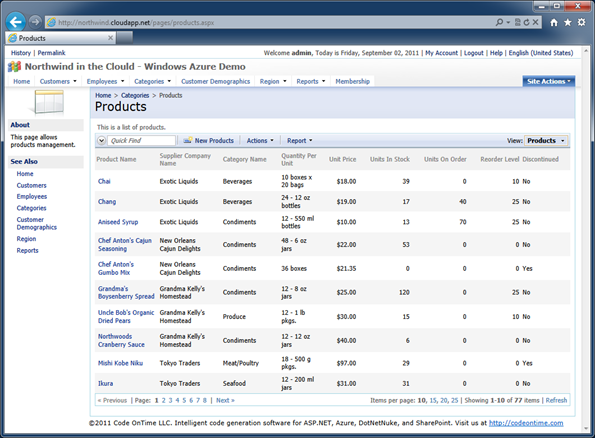
Powerful and simple mechanism of data controller URL parameters allows easy manipulation of the page behavior in Code On Time web applications. For example, consider Products page at http://northwind.cloudapp.net/pages/products.aspx. If you navigate to the page and login as admin/admin123% then you will see the following screen with a list of products.
If you want to navigate to a specific product then try the following link. The same page will open in edit mode on the product with the primary key equal to 7.
http://northwind.cloudapp.net/pages/products.aspx?ProductID=7&_controller=Products&_commandName=Edit&_commandArgument=editForm1
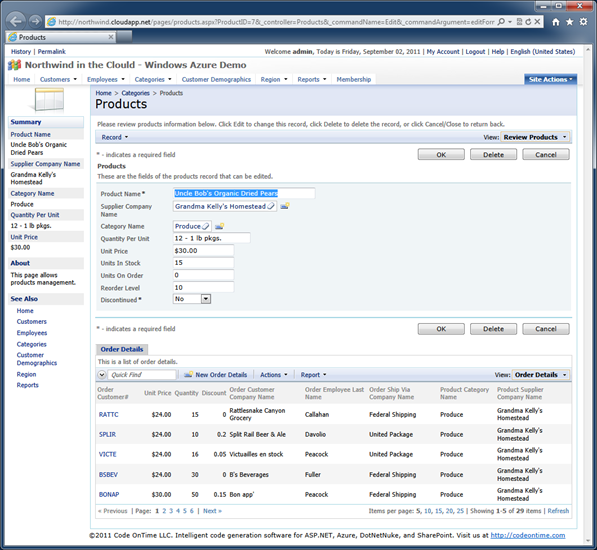
Data controller parameters offer a simple and powerful method of affecting user interface presentation. Couple that with robust Access Control Rules implementation and your web app will provide an excellent and secure mechanism of navigation to specific records.
Sometimes you may want to prevent any possibility of external commands sent to your application via URL parameters unless the commands were initiated by the web application itself or an external “friendly” source.
Enabling URL Hashing
Unlimited edition of Code On Time offers a new feature called URL Hashing, which is available as a component of EASE (Enterprise Application Services Engine). The purpose of URL Hashing is to ensure that only encrypted commands can be passed in the URL of your web application.
Start the web application generator, select your project and click Next button a few times until your reach the Features page. Enable URL Hashing under EASE Configuration.
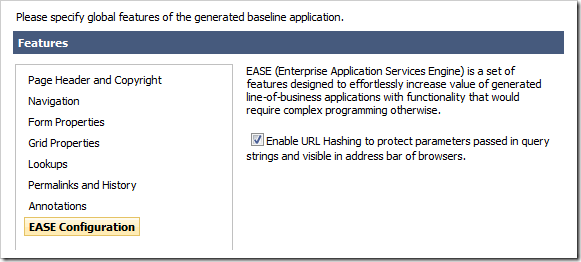
Proceed to generate the project.
Navigate to any page of your web application displaying data and try passing any parameter in the URL. For example, if you are looking at Products.aspx page then change the URL in the address bar of the browser to Products.aspx?AnyParam=Hello and hit enter key to navigate to the page.
You will see the following response.
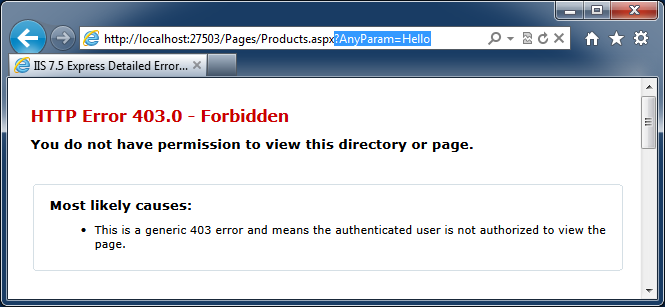
All applications pages are now protected and will not allow inclusion of any URL parameters.
Internal URL Parameters
Your web application may be using URL parameters for its own purpose. For example, configure a Navigate action in the Northwind sample as explained next.
Select your project on the start page of the web app generator and click Design. Select Products data controller on All Controllers tab and activate Action Groups page.
Select action group ag1 with the scope of Grid and switch to Actions tab.
Add a new action with the following properties. Note that Command Argument must be entered without line breaks.
| Property | Value |
| Command Name | Navigate |
| Command Argument | ?ProductID={ProductID}&_controller=Products&_commandName=Edit&_commandArgument=editForm1 |
| Header Text | Edit Product |
The value of command argument instructs the application to navigate to the current page that hosts the data controller view and pass the ProductID of selected row in the URL. The other URL parameters will force the data controller to open the specified product in editForm1 in Edit mode.
Save the new action, exit the Designer and generate your project.
Navigate to Products page and select the context menu of a product row.
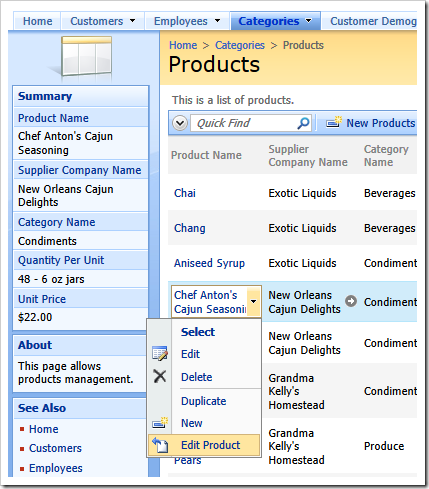
Your browser will navigate to the currently active page with the URL that looks as follows. Notice that there is a parameter “_link” with the cryptic looking value in the address bar of the browser.
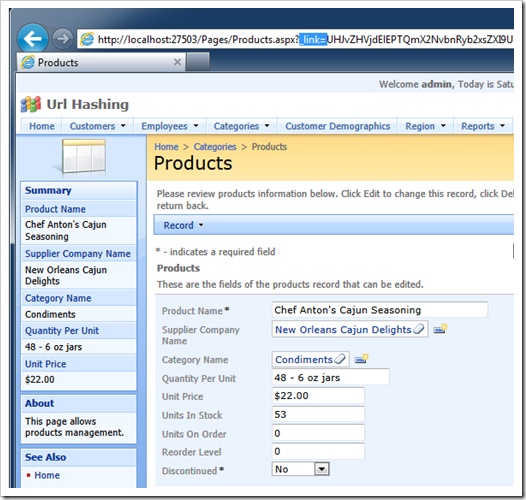
URL Hashing mechanism embedded in your application only allows this particular parameter and demands that the value of “ _link” parameter is encrypted.
Alter any portion of the parameter or add any additional URL parameters and the request will fail to display the page with the same HTPP error code 403 presented above.
External URL Parameters
Sometimes you may need to pass URL parameters from an external web application. If URL Hashing feature is enabled then this task becomes impossible unless you encrypt the URLs passed by external web application.
The implementation of encryption can be found in the StringEncryptorBase class of your application source code. The partial code below shows encryption key (Key) and initialization vector (IV). Both properties are passed by methods Encrypt and Decrypt as arguments to the default implementation of Advanced Encryption Standard (AES) available in Microsoft.NET Framework.
C#:
public class StringEncryptorBase
{
public virtual byte[] Key
{
get
{
return new byte[] {
253,
124,
8,
201,
31,
27,
89,
. . . .
153};
}
}
public virtual byte[] IV
{
get
{
return new byte[] {
87,
84,
163,
98,
205,
. . . .
112};
}
}
public virtual string Encrypt(string s)
{
. . . . . .
}
public virtual string Decrypt(string s)
{
. . . . . .
}
}
VB:
Public Class StringEncryptorBase
Public Overridable ReadOnly Property Key() As Byte()
Get
Return New Byte() {253, 124, . . . ., 153}
End Get
End Property
Public Overridable ReadOnly Property IV() As Byte()
Get
Return New Byte() {87, 84, 163, 98, . . . ., 112}
End Get
End Property
Public Overridable Function Encrypt(ByVal s As String) As String
. . . . .
End Function
Public Overridable Function Decrypt(ByVal s As String) As String
. . . . .
End Function
End Class
Copy this class to the external application and make sure to encrypt the URLs that are passed to a Code On Time web application with URL Hashing enabled.
You may also want to change the key and initialization vector. The default values are hard-coded and shared by all applications generated with Unlimited edition of Code On Time.
Conclusion
URL Hashing is always performed for History and permalinks. If the application is generated without URL Hashing enabled then the permalinks are simply encoded with base-64 encoding to mask the nature of URL parameters.
Advanced encryption with hash code validation will be performed on links create with View Details command and on results of any actions with Command Name set to Navigate.