Application security, especially controlling who sees what data, is often a complex and time-consuming task. Developers traditionally wade through lines of code or repetitive configurations to implement row-level security, making it prone to errors and difficult to audit. What if you could define and test these critical data access rules visually, getting instant feedback and ensuring your application is locked down precisely as intended, all without writing a single line of server-side code for most common scenarios?
Introducing Static Access Control Rules (SACR) in Code On Time, now supercharged by the integrated App Studio 2025. We've taken the power of declarative, SQL-based security and paired it with an intuitive visual interface. Imagine defining rules like "users only see their own orders" or "managers in the Sales department can only see customers in their region" through a simple point-and-click configuration, directly within your live application preview. No more hunting through business rule files or worrying if your custom code covers every edge case for standard security patterns!
With App Studio, configuring SACR becomes a breeze. See at a glance which parts of your application are protected with clear visual cues like the "security shield" icon directly in the App Explorer. Define rules using straightforward properties, get instant feedback on their impact, and even use the "Related Items" feature to see exactly which data fields and views are affected by a specific rule. Debugging is simplified to toggling a rule's Enabled status and observing the change immediately. This visual approach not only accelerates development but also makes your security posture transparent and significantly easier to maintain.
Ready to transform how you handle data security? Stop wrestling with complex code for common security needs and embrace the power of visual configuration. Learn how to master Static Access Control Rules with our comprehensive tutorial and start building more secure applications, faster.
Click here to learn how to master Static Access Control Rules with our comprehensive tutorial.
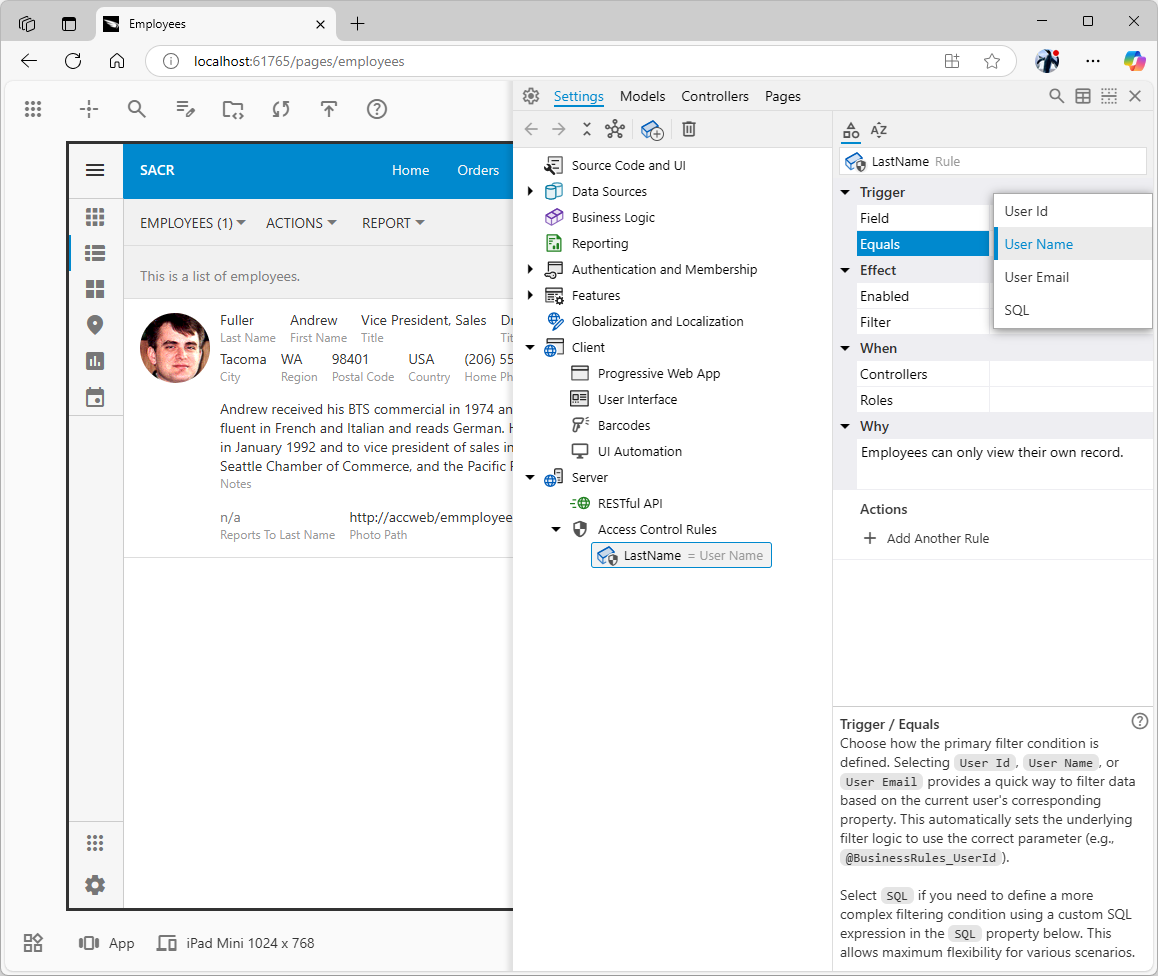 This access control rule is triggered by the presence of the
This access control rule is triggered by the presence of the LastName data field in the view. The framework will filter in the rows that have the trigger field value that matches the user’s name. The rule applies to the views of all existing and future data controllers of the application.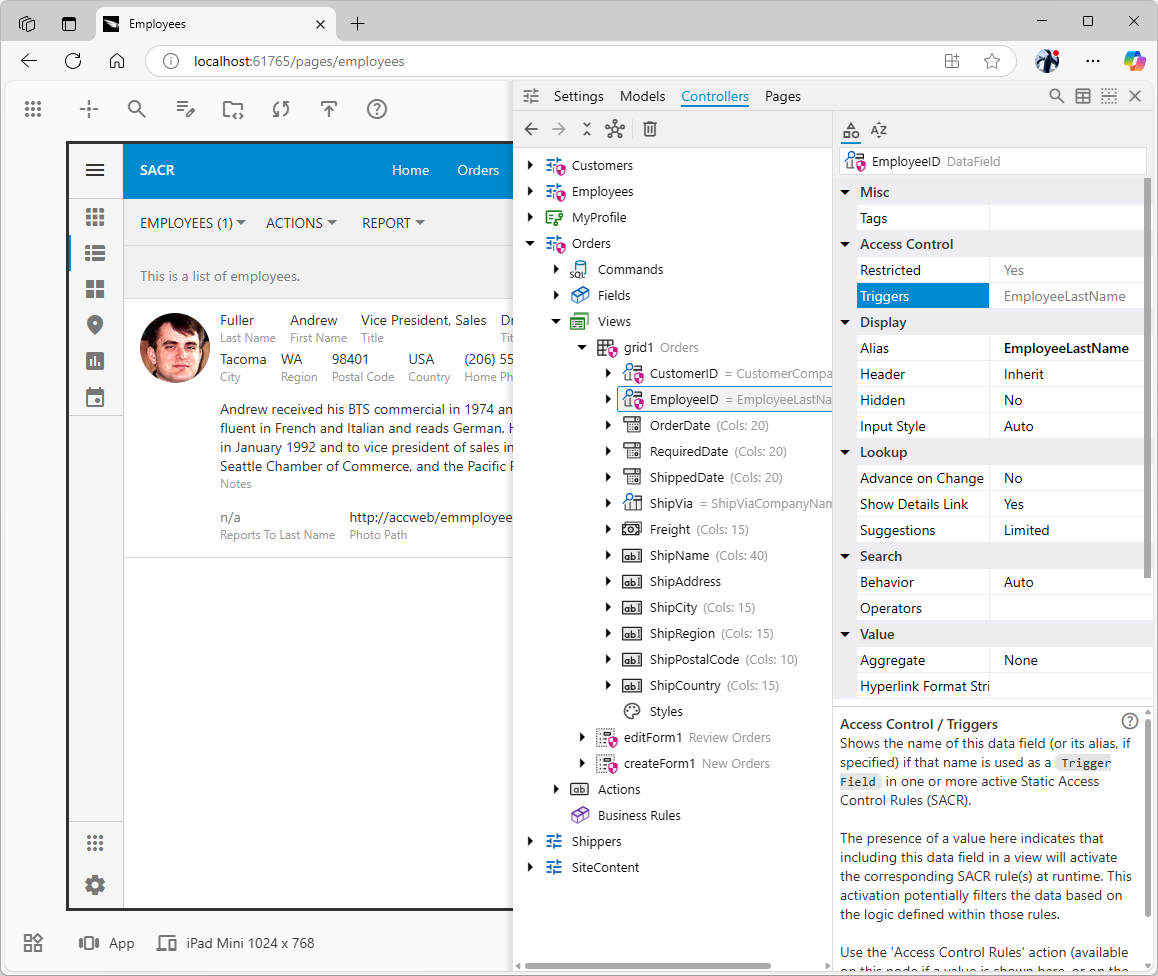 The maroon “security shield” icon is overlaid on the relevant configuration nodes of
The maroon “security shield” icon is overlaid on the relevant configuration nodes of Customers, Employees, and Orders data controllers. The icon subtly hints of the security restrictions in the application making it possible at-a-glance security check. The Access Control property group of the affected nodes contains the Triggers property with the list of relevant “trigger” fields defined in SACR.